
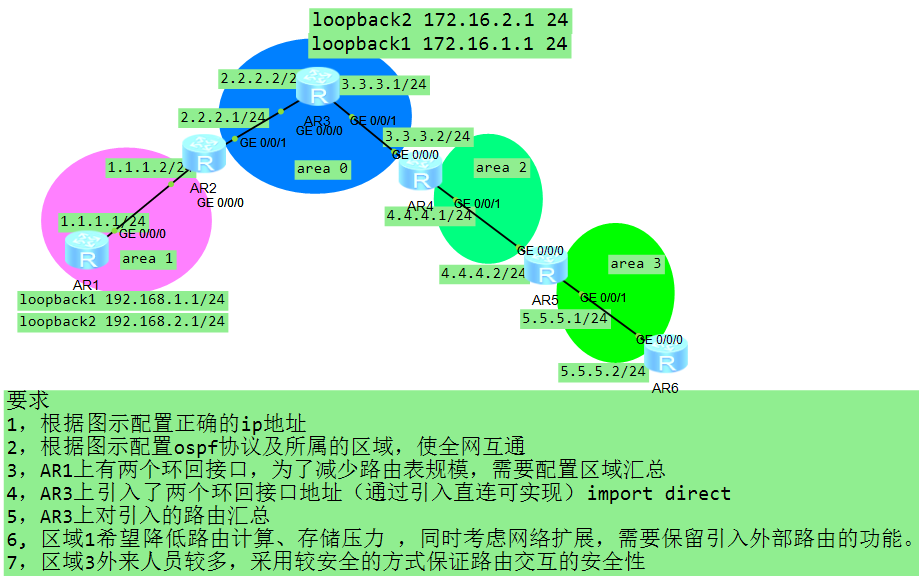
拓扑
要求:
1,根据图示配置正确的ip地址
2,根据图示配置ospf协议及所属的区域,使全网互通
3,AR1上有两个环回接口,为了减少路由表规模,需要配置区域汇总
4,AR3上引入了两个环回接口地址(通过引入直连可实现)import direct
5,AR3上对引入的路由汇总
6,区域1希望降低路由计算、存储压力 ,同时考虑网络扩展,需要保留引入外部路由的功能。
7,区域3外来人员较多,采用较安全的方式保证路由交互的安全性
配置记录简述:
1、配置ip地址:略过不写。
2、宣告ospf各区,由于area3 不与骨干区area0 直接连接无法学习到其他区域的ospf路由,这里需要用到虚链路 vlink-peer,配置简述:area2 下 ar4 配置route-id 4.4.4.4 , ar5配置route-id 5.5.5.5;ospf下ar4 area2 配置vlink-peer 5.5.5.5 ,下ar5 area2 配置vlink-peer 4.4.4.4 使area3建立虚链路与骨干区直接相连。
3、area1下的abr(ar2)设置路由汇总 abr-summary 192.168.0.0 255.255.252.0 讲两个环回接口的路由汇总成一条。
4、ar3下的两个环回接口引入直连路由,ar3作为asbr(自治系统边界路由器)引入外部路由,ospf 下配置: import-route direct。
5、asbr-summary 172.16.0.0 255.255.252.0 路由汇总。
6、ar1 ,ar2 在区域1 下分别配置 nssa ,干掉 4 5 类lsa 保留外部路由。
7、区域3,ar5 和 ar6 分别ospf area3 配置authentication-mode md5 1 cipher admin
所有route的配置:
[V200R003C00]
#
sysname ar1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 1.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 192.168.1.1 255.255.255.0
#
interface LoopBack2
ip address 192.168.2.1 255.255.255.0
#
ospf 1
area 0.0.0.1
network 1.1.1.0 0.0.0.255
network 192.168.1.0 0.0.0.255
network 192.168.2.0 0.0.0.255
nssa
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<ar1>
--------------------------------------------------------
<ar2>disp cur
<ar2>disp current-configuration
[V200R003C00]
#
sysname ar2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 1.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 2.2.2.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ospf 1
area 0.0.0.0
network 2.2.2.0 0.0.0.255
area 0.0.0.1
abr-summary 192.168.0.0 255.255.252.0
network 1.1.1.0 0.0.0.255
nssa
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<ar2>
--------------------------------------------------------
<ar3>disp cur
[V200R003C00]
#
sysname ar3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
ospfv3 1
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 2.2.2.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 3.3.3.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 172.16.1.1 255.255.255.0
#
interface LoopBack2
ip address 172.16.2.1 255.255.255.0
#
ospf 1
asbr-summary 172.16.0.0 255.255.252.0
import-route direct
area 0.0.0.0
network 2.2.2.0 0.0.0.255
network 3.3.3.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<ar3>
--------------------------------------------------------
<ar4>disp cu
[V200R003C00]
#
sysname ar4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 3.3.3.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 4.4.4.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 44.44.44.44 255.255.255.0
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 3.3.3.0 0.0.0.255
area 0.0.0.2
network 4.4.4.0 0.0.0.255
vlink-peer 5.5.5.5
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<ar4>
--------------------------------------------------------
<ar5>disp cur
[V200R003C00]
#
sysname ar5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 4.4.4.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 5.5.5.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 55.55.55.55 255.255.255.0
#
ospf 1 router-id 5.5.5.5
area 0.0.0.2
network 4.4.4.0 0.0.0.255
vlink-peer 4.4.4.4
area 0.0.0.3
authentication-mode md5 1 cipher %$%$>g}P.Dx'yG#4|05aM->+ONqz%$%$
network 5.5.5.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<ar5>
-------------------------------------------------------
<ar6>disp cur
[V200R003C00]
#
sysname ar6
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 5.5.5.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ospf 1
area 0.0.0.3
authentication-mode md5 1 cipher %$%$Z9fIL=J(P)F1XG)Q[$!,OOK!%$%$
network 5.5.5.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return结束,谢谢阅读。


看样子,肯定是准备考华为的证啊
对的呀
玩技e族来看看
欢迎常来 O(∩_∩)O